The Weak Security and Privacy Warning on the iOS14 or iOS15
Archer C5400 , RE270K , RE715X , Archer TX55E , Deco BE65-5G , Archer C2 , Archer AX95 , RE205 , Archer AX96 , Archer TX20UH , Archer VR1200v , Deco Voice X50 , Deco E4R , Deco E4S , M7350 , Deco X4300 Pro , Archer GE550 , Archer BE850 , Deco W6000 , Archer C8 , Archer C9 , Archer C6 , Archer C7 , RE210 , Archer AX90 , RE330 , Archer CR700 , RE450 , Archer C5400X , RE315 , Deco X50-PoE , Archer A1200 , Archer T2UH , M7000 , RE500XD , TL-WA850RE , Deco WB10800 , Deco W7200 , Archer T3U Nano , Archer AX80 , Archer VR400 , RE200 , RE105 , Archer AX4200 , Archer XR500v , Archer A2 , Archer AX75 , Archer AX73 , Archer VR2100 , Deco PX50 , Archer VR2800v , Deco BE95 , Archer VR1210v , Deco BE65 Pro , RE350 , Archer A6 , Archer A7 , Archer AX72 , Archer A5 , TL-MR150 , Deco X90 , Archer A8 , Archer A9 , RE230 , Deco W2400 , RE215 , Archer AX68 , Deco X95 , RE335 , RE455 , RE605X , Archer AX5300 , Deco X96 , Deco XM73 , Archer Air R5 , Deco XE75 Pro , TL-MR3040 , Archer AXE300 , Archer AX1500 , Archer BE700 , Archer AX60 , Archer VR300 , RE220 , Deco M3W , Archer AX3000 , Deco W3600 , RE400 , Archer A2600 , Archer AX55 , Deco X50-DSL , Archer T4E , RE505X , Archer AX53 , Deco X68 , Archer AX51 , Archer VR2800 , Archer MR550 , TL-MR6400 , TL-WA860RE , Deco X5700 , Archer T4U , Archer BE11000 Pro , Archer AX50 , Deco M5 , RE650 , Deco M4 , Deco HX20 , Deco M3 , Archer AX6000 , RE603X , Deco X75 , Archer TBE550E , Archer C24 , Archer TX20U Plus , DecoX5700 , Deco X50-4G , RE700X , RE1750X , Archer T4UH , Archer C21 , Archer TX50E , Archer C20 , RE780X , Archer MR200 , Archer T3U , TL-MR3020 , Archer MR202 , RE700K , Archer AX1800 , Deco X50-Outdoor , Deco X73-DSL , Archer BE800 , Archer VR200 , Deco X50-5G , Archer BE3600 , Deco X80 , Archer T2E , Archer BE7200 , RE300 , Archer C900 , Archer AX4400 , RE305 , RE600X , Archer C50
Recent updates may have expanded access to feature(s) discussed in this FAQ. Visit your product's support page, select the correct hardware version for your device, and check either the Datasheet or the firmware section for the latest improvements added to your product. Please note that product availability varies by region, and certain models may not be available in your region.
issue Description/Phenomenon:
Ever since IOS 14 updates(https://support.apple.com/en-us/HT211808 ), Apple has made great changes on the security update on IOS devices. New Privacy features improve user transparency and control over how apps access your location, photos, microphone, and camera.
After that, sometimes you might get a "Privacy warning" or "Weak Security" on your Wi-Fi network.
Case 1: Weak Security
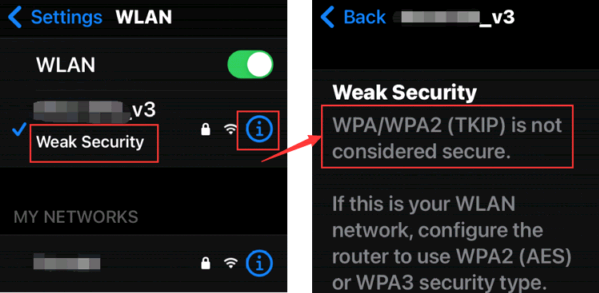
The following security modes have been considered insecure by Apple. So when IOS devices detect any of them was used by your router, the weak security will pop out.
( https://support.apple.com/en-us/HT202068 )
-
WPA/WPA2 mixed modes
-
WPA Personal
-
WEP, including WEP Open, WEP Shared, WEP Transitional Security Network, or Dynamic WEP (WEP with 802.1X)
-
TKIP, including any security setting with TKIP in the name
Solution:
Change your router security to be one of the following:
WPA3 Personal; WPA2/WPA3 Transitional or WPA2 Personal (AES)
Currently, All TP-Link routers supported changing wireless security, and please update to the latest firmware to improve your security.
Note: For the Archer C60 V2, please contact support.
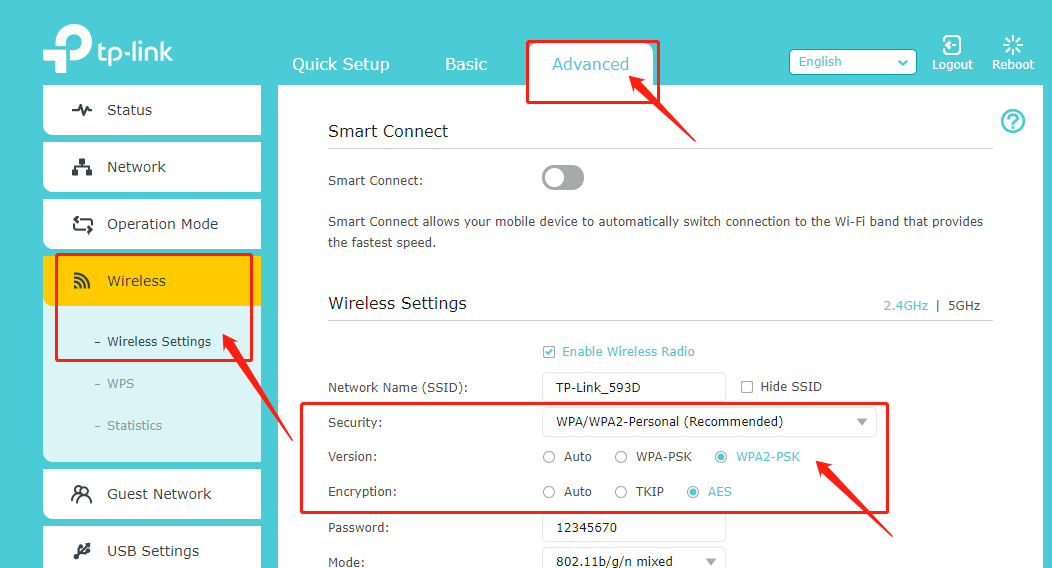
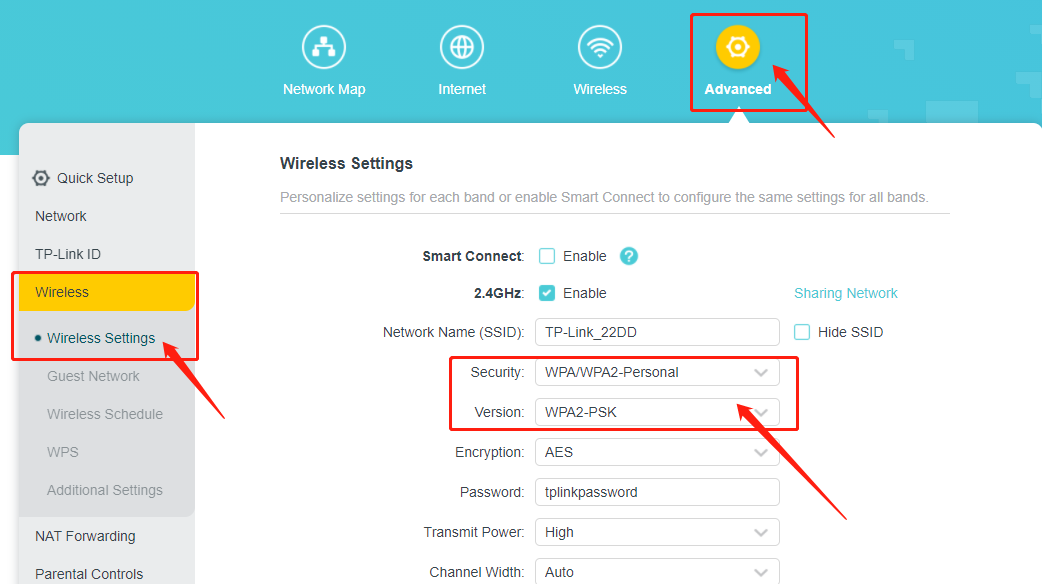
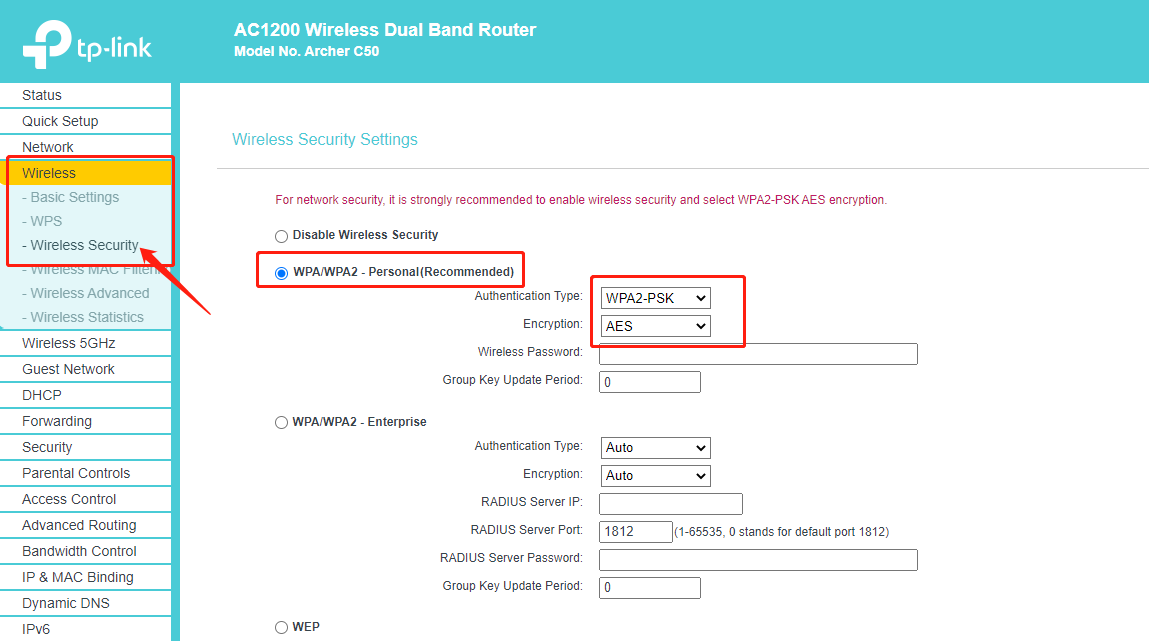
1. For TP-Link Router
Please log in to your Router’s web interface, referring to How do I log into the web-based Utility (Management Page) of TP-Link wireless router?
On the web interface, please go to Advanced -> Wireless -> Wireless settings -> change the security type to WPA2-PSK -> click on the save button to finish the setting.
Archer Series (take Archer C9 as an example):
WiFi6 Series (take AX 1500 as an example):
TL-WR841N and Archer C50, C55:
2. For Deco Series
Deco models allow you to change the wireless security type on the Deco app, and please update the Deco app and the Deco’s firmware to the latest one if you do not see this feature.
NOTE: For the Deco M9 Plus with 1.2.12 or earlier firmware version, please refer to Method 3 in the link to update the firmware via the Upgrade Tool.
Take Deco M4 as an example.
You can go to the Deco app >More >Wi-Fi Settings >Security to change the wireless security type.
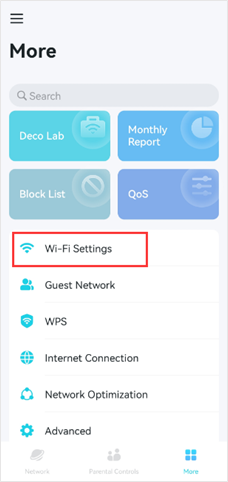
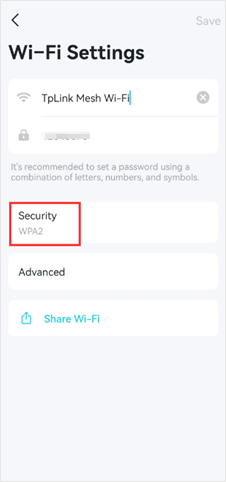
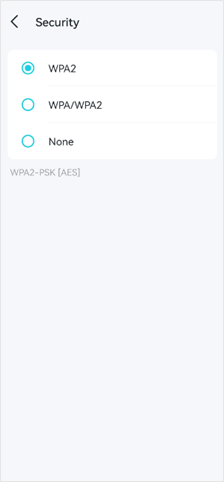
3. For Range Extenders
(1) it is recommended to change the encryption method of the front-end router or main AP to WPA2 + AES;
(2) then upgrade the firmware of the Range Extender to the newest on the official support page;
(3) then reset and reconfigure the Range Extender after upgrading to the newest firmware. Set the SSID of the Range Extender to a new one for checking, it's more recommended to configure through the webpage. Then Reboot the router and Range Extender together after that.
4. For MiFi products
1) M7200 V2&V3, M7450 V2, M7650 V1.1:
The latest official firmware has already set AES as the default encryption, please upgrade the firmware to the latest version, no need to change security manually.
2) M7650 V1, M7450 V1, M7350 V5, M7200 V1, M7000 V1, M7300 V3:
The default Wi-Fi security setting is WPA-PSK/WPA2-PSK Auto, please change it to WPA-PASK/WPA2-PSK AES. If you cannot see this option, please make sure you are using the latest firmware
3) M7350 V3&V4, M7310 V1&V2, M7300 V2:
The default Wi-Fi security setting is WPA-PSK/WPA2-PSK Auto, there is no option to set AES only.
[Note]:
The default Wi-Fi encryption on our products is set to Auto, which supports AES as well, the secure encryption method, and also supports TKIP encryption to be compatible with the devices that only support TKIP encryption.
It doesn't mean Apple must use the weak encryption method when it says weak security. If set the encryption to AUTO or TKIP mix AES, iOS devices will actively choose the secured encryption method WPA2+AES, but still give you a warning. So please don’t worry about its security.
Case 2: Privacy Warning about private WLAN address being turned off.
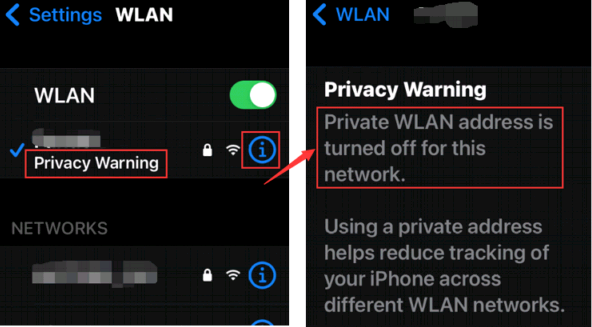
Cause: It happens because the iOS uses its real MAC address to communicate.
Suggestion:
To improve privacy, Apple suggested keeping private addresses enabled all the time so that your device would use a different MAC address with each Wi-Fi network. ( https://support.apple.com/en-us/HT211227 )
Note: Though It will stop someone from tracking your network activity, some users reported that their IOS devices were “unknown” to routers since the random MAC address could not be recognized by the manufacturer anymore. The related issue has been discussed already, such as:
https://community.netgear.com/t5/Nighthawk-WiFi-Routers/Unknown-Attached-Device/m-p/2005741
https://community.tp-link.com/us/home/forum/topic/515526
Case 3: Privacy Warning about not supporting encrypted DNS.
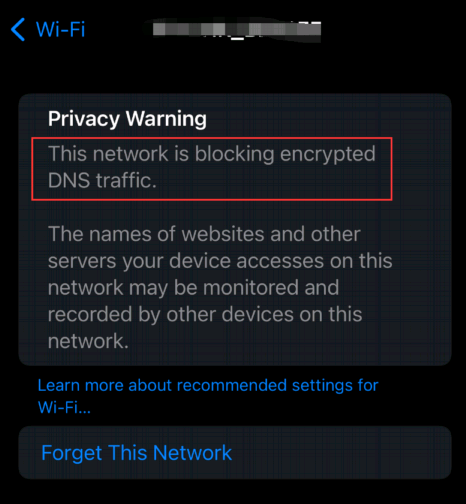
Cause: This iOS privacy feature is meant to be used where the router and the router's handling of DNS cannot be trusted, so it is designed to circumvent whatever the router is doing.
Solutions:
Deco has a special way to deal with its DNS requests, and when you had this notification.
Please set the DNS server to 8.8.8.8 and 1.1.1.1 manually in Deco App > More > Internet Connection > IPv4 page refers to this link, then go to the Wi-Fi setting of your IOS devices, forget/delete the Deco’s network, and reconnect to it again.
Is this faq useful?
Your feedback helps improve this site.
What’s your concern with this article?
- Dissatisfied with product
- Too Complicated
- Confusing Title
- Does not apply to me
- Too Vague
- Other
Thank you
We appreciate your feedback.
Click here to contact TP-Link technical support.
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.
We have updated our Policies. Read Privacy Policy and Terms of Use here.
This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy .
We have updated our Policies. Read Privacy Policy and Terms of Use here.
This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy .
Basic Cookies
These cookies are necessary for the website to function and cannot be deactivated in your systems.
TP-Link
accepted_local_switcher, tp_privacy_base, tp_privacy_marketing, tp_smb-select-product_scence, tp_smb-select-product_scenceSimple, tp_smb-select-product_userChoice, tp_smb-select-product_userChoiceSimple, tp_smb-select-product_userInfo, tp_smb-select-product_userInfoSimple, tp_top-banner, tp_popup-bottom, tp_popup-center, tp_popup-right-middle, tp_popup-right-bottom, tp_productCategoryType
Livechat
__livechat, __lc2_cid, __lc2_cst, __lc_cid, __lc_cst, CASID
Youtube
id, VISITOR_INFO1_LIVE, LOGIN_INFO, SIDCC, SAPISID, APISID, SSID, SID, YSC, __Secure-1PSID, __Secure-1PAPISID, __Secure-1PSIDCC, __Secure-3PSID, __Secure-3PAPISID, __Secure-3PSIDCC, 1P_JAR, AEC, NID, OTZ
Analysis and Marketing Cookies
Analysis cookies enable us to analyze your activities on our website in order to improve and adapt the functionality of our website.
The marketing cookies can be set through our website by our advertising partners in order to create a profile of your interests and to show you relevant advertisements on other websites.
Google Analytics & Google Tag Manager
_gid, _ga_<container-id>, _ga, _gat_gtag_<container-id>
Google Ads & DoubleClick
test_cookie, _gcl_au
Meta Pixel
_fbp
Crazy Egg
cebsp_, _ce.s, _ce.clock_data, _ce.clock_event, cebs
lidc, AnalyticsSyncHistory, UserMatchHistory, bcookie, li_sugr, ln_or


