What should I do if I got a certificate error?
CPE510 , EAP225 V3 , CPE610 , CPE220 , EAP225-Wall , CPE210 , CPE520 , EAP225-Outdoor , EAP225 V2 , EAP245 , EAP320 , EAP110 , EAP220 , EAP330 , EAP120 , EAP235-Wall , WBS510 , EAP115 , EAP225 , WBS210 , EAP110-Outdoor , Omada Software Controller , EAP115-Wall , CPE605
Recent updates may have expanded access to feature(s) discussed in this FAQ. Visit your product's support page, select the correct hardware version for your device and check either the Datasheet or the firmware section for the latest improvements added to your product.
Part 1: For EAP and CPE web management interface
When try to visit the web interface via https in Chrome, such as the web interface of EAP/Omada Controller or Pharos CPE Series, it said server’s certificate is not trusted.
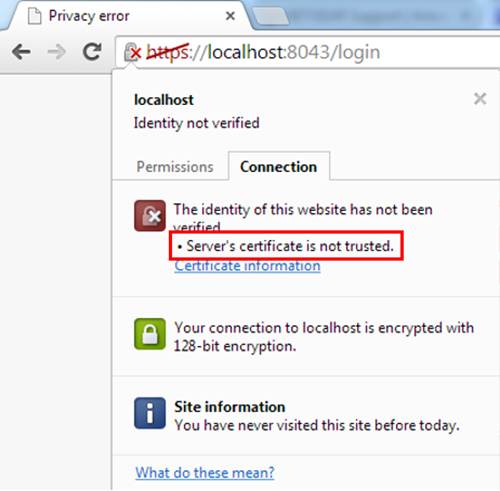
The certificate refers to how public websites trust each other. It is safe enough since we can make sure the IP address to be the same of the server’s.
Here are two examples for how to get through the certificate error when it occurred on TP-Link products.
1. Get through Certificate error on Chrome
Click on Advanced -- Proceed to localhost (unsafe), the web interface of EAP/Omada Controller will show up.


2. Get through Certificate error on Internet Explorer
While in Internet Explorer, you can just click on Continue to this website (not recommended) to visit the web interface.

Part 2: For EAP/Omada controller
For the EAP devices, its certificate can’t be changed; while for the EAP/Omada controller, you can manually import your own certificate if you have one.
Here are the instructions:
1. Disable the EAP/Omada controller on your computer.
2. Copy your keystore file (such as keystore.jks file) into the “keystore” folder of the EAP/Omada controller’s installation path.
3. Enter the “properties” folder of EAP/Omada controller installation path, edit the “jetty.properties” file.
4. Find the scripts below:
ssl.key.store.password=tplink
ssl.manager.password=tplink
ssl.trust.store.password=tplink
key.store.path=/keystore/eap.keystore
trust.store.path=/keystore/eap.keystore
5. Replace the scripts above with new scripts as below:
ssl.key.store.password= the storepass of your own certificate
ssl.manager.password= the keypass of your own certificate
ssl.trust.store.password= the storepass of your own certificate
key.store.path=/keystore/keystore.jks(your keystore file)
trust.store.path=/keystore/keystore.jks(your keystore file)
6. Launch the EAP controller, then you can use your domain name according to your certificate to visit the controller, such as https://hostname:8043, please note that the IP of hostname should be the IP of the controller PC.
Looking for More
Is this faq useful?
Your feedback helps improve this site.
What’s your concern with this article?
- Dissatisfied with product
- Too Complicated
- Confusing Title
- Does not apply to me
- Too Vague
- Other
We'd love to get your feedback, please let us know how we can improve this content.
Thank you
We appreciate your feedback.
Click here to contact TP-Link technical support.
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.
This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy . Don’t show again
This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy . Don’t show again
Basic Cookies
These cookies are necessary for the website to function and cannot be deactivated in your systems.
TP-Link
SESSION, JSESSIONID, accepted_local_switcher, tp_privacy_base, tp_privacy_marketing, tp_smb-select-product_scence, tp_smb-select-product_scenceSimple, tp_smb-select-product_userChoice, tp_smb-select-product_userChoiceSimple, tp_smb-select-product_userInfo, tp_smb-select-product_userInfoSimple, tp_top-banner, tp_popup-bottom, tp_popup-center, tp_popup-right-middle, tp_popup-right-bottom, tp_productCategoryType
Youtube
id, VISITOR_INFO1_LIVE, LOGIN_INFO, SIDCC, SAPISID, APISID, SSID, SID, YSC, __Secure-1PSID, __Secure-1PAPISID, __Secure-1PSIDCC, __Secure-3PSID, __Secure-3PAPISID, __Secure-3PSIDCC, 1P_JAR, AEC, NID, OTZ
Zendesk
OptanonConsent, __cf_bm, __cfruid, _cfuvid, _help_center_session, _pendo___sg__.<container-id>, _pendo_meta.<container-id>, _pendo_visitorId.<container-id>, _zendesk_authenticated, _zendesk_cookie, _zendesk_session, _zendesk_shared_session, ajs_anonymous_id, cf_clearance
Analysis and Marketing Cookies
Analysis cookies enable us to analyze your activities on our website in order to improve and adapt the functionality of our website.
The marketing cookies can be set through our website by our advertising partners in order to create a profile of your interests and to show you relevant advertisements on other websites.
Google Analytics & Google Tag Manager
_gid, _ga_<container-id>, _ga, _gat_gtag_<container-id>
Google Ads & DoubleClick
test_cookie, _gcl_au










_EU_3.0_2401__normal_20240119043538b.png)