How to limit specific IP to access to internal server by TP-LINK SMB router
TL-R600VPN , TL-ER6120 , TL-ER6020 , TL-ER5120 , TL-R480T+ , TL-R470T+ , TL-ER604W
Recent updates may have expanded access to feature(s) discussed in this FAQ. Visit your product's support page, select the correct hardware version for your device, and check either the Datasheet or the firmware section for the latest improvements added to your product. Please note that product availability varies by region, and certain models may not be available in your region.
Application Scenario
In some cases, we just want only some specific external IPs to access internal server behind TP-LINK SMB Router. This demands can be met by Virtual Server with Access Control.
Now we take TL-ER6120 v2 as an example. The Web server is behind TL-ER6120 LAN port as 192.168.0.2:8080. And client is located in 14.28.137.216 out of WAN1. We only want to make external IP 14.28.137.216 be able to access this server. Our topology is connected as follow.
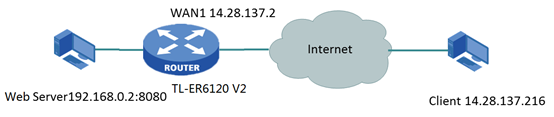
How can we achieve that?
TL-ER6120 is NAT device. Web server is on 192.168.0.2:8080 behind TL-ER6120. First of all we open port of 8080 about 192.168.0.2 for all external IP. And then we configure Access Control to limit only IP 14.28.137.216 to access to Web server. The specific configuration steps are as follows.
Step 1
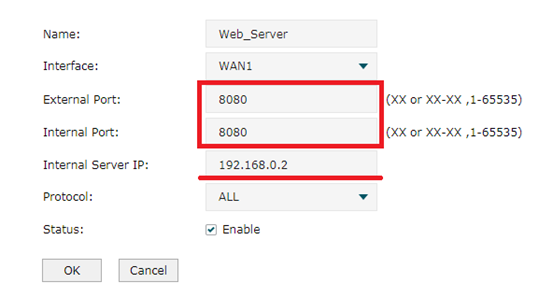
This step we need to open ports of 8080. Go to Advanced---->NAT----->Virtual Server. For interface, we select WAN1 and set port as 8080. Internal Server IP is 192.168.0.2. Click OK then. When finished, there will form a rule entry in Virtual Server List.
Step 2
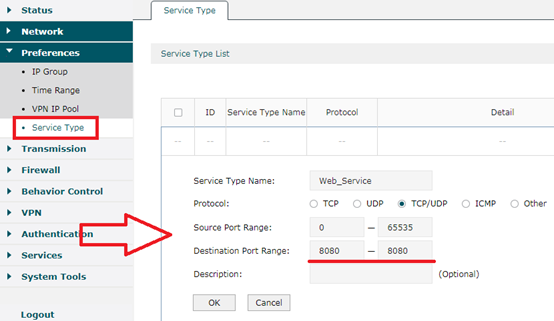
This step we configure Service Type to match Web server port 8080. Turn to Preferences---->Service Type. Name service type as Web Service. And Select Protocol TCP/UDP. Source Port Range is 0-65535. Fill in destination port as 8080. Click OK.
Step 3
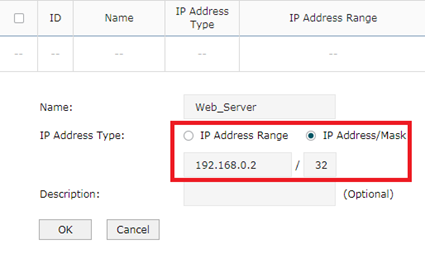
This step let’s configure IP group. Turn to Preferences----->IP Group---->IP address. Add entry as above.
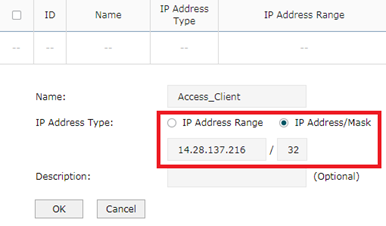
Access_Client is the same with Web_Server. Then there will be two new entries in IP Address List.
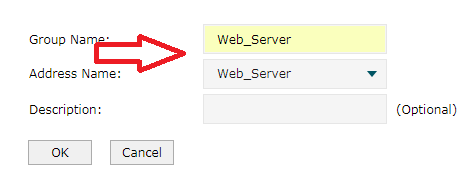
Turn to IP Group. Corresponds to the Address Name and Group Name. Set according to the picture respectively.
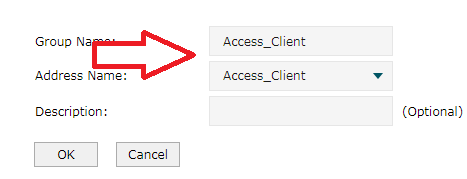
This step is simple. Match Access_Client with Access_Client Group then.
Step 4 Let’s configure Access Control now.
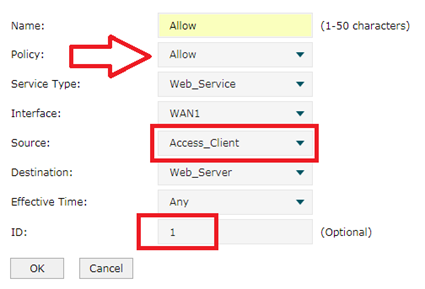
On Firewall---->Access Control, set as the picture above. We select Allow Policy first and choose Web_Service we just now set up for 8080 port for Service Type. In Source option, we select IP Group-- Access_Client we set before. In destination we choose Web_Server. ID as 1. Then click OK.
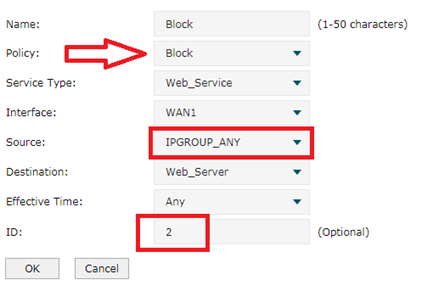
And then we configure a Block policy. The policy is Block and Source is IPGROUP_ANY. Don’t forget set ID as 2. Click OK.
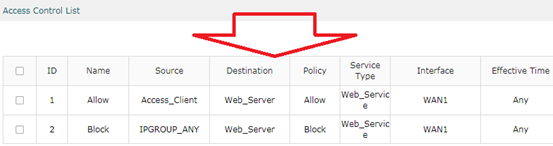
After finishing, there will be two entries in List of Rules.
Verification
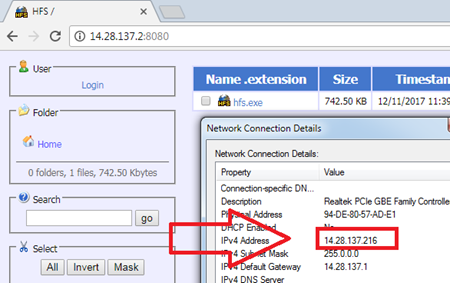
As the screenshot above, on client 14.28.137.216 we type in 14.28.137.2:8080. (14.28.137.2 is WAN1 address) We’ll find it can access Web server normally.
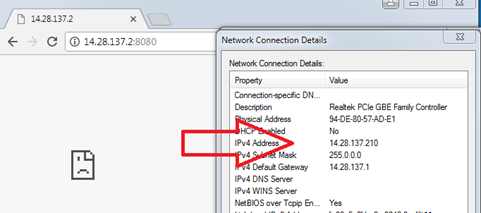
And on any other client like 14.28.137.210, we cannot access Web server. It works as expected!
Note:
1. The ID order of Access Control List present the priority and it is important.
2. TL-R600VPN could meet demands only with hardware version v4.
3. For other models’ different hardware versions, there will be different UI. The configuration process of different UI is the same as the example’s UI basically. Lack of IP Group configuration, other configuration options just changed position.
Looking for More
Is this faq useful?
Your feedback helps improve this site.
What’s your concern with this article?
- Dissatisfied with product
- Too Complicated
- Confusing Title
- Does not apply to me
- Too Vague
- Other
Thank you
We appreciate your feedback.
Click here to contact TP-Link technical support.
TP-Link Community
Still need help? Search for answers, ask questions, and get help from TP-Link experts and other users around the world.
This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy . Don’t show again
This website uses cookies to improve website navigation, analyze online activities and have the best possible user experience on our website. You can object to the use of cookies at any time. You can find more information in our privacy policy . Don’t show again
Basic Cookies
These cookies are necessary for the website to function and cannot be deactivated in your systems.
TP-Link
SESSION, JSESSIONID, accepted_local_switcher, tp_privacy_base, tp_privacy_marketing, tp_smb-select-product_scence, tp_smb-select-product_scenceSimple, tp_smb-select-product_userChoice, tp_smb-select-product_userChoiceSimple, tp_smb-select-product_userInfo, tp_smb-select-product_userInfoSimple, tp_top-banner, tp_popup-bottom, tp_popup-center, tp_popup-right-middle, tp_popup-right-bottom, tp_productCategoryType
Youtube
id, VISITOR_INFO1_LIVE, LOGIN_INFO, SIDCC, SAPISID, APISID, SSID, SID, YSC, __Secure-1PSID, __Secure-1PAPISID, __Secure-1PSIDCC, __Secure-3PSID, __Secure-3PAPISID, __Secure-3PSIDCC, 1P_JAR, AEC, NID, OTZ
Zendesk
OptanonConsent, __cf_bm, __cfruid, _cfuvid, _help_center_session, _pendo___sg__.<container-id>, _pendo_meta.<container-id>, _pendo_visitorId.<container-id>, _zendesk_authenticated, _zendesk_cookie, _zendesk_session, _zendesk_shared_session, ajs_anonymous_id, cf_clearance
Analysis and Marketing Cookies
Analysis cookies enable us to analyze your activities on our website in order to improve and adapt the functionality of our website.
The marketing cookies can be set through our website by our advertising partners in order to create a profile of your interests and to show you relevant advertisements on other websites.
Google Analytics & Google Tag Manager
_gid, _ga_<container-id>, _ga, _gat_gtag_<container-id>
Google Ads & DoubleClick
test_cookie, _gcl_au










